Apk decompiler. It’s comparatively simple to decompile an APK and read its contents. this article will assist you to perceive how a hacker will approach your APK.
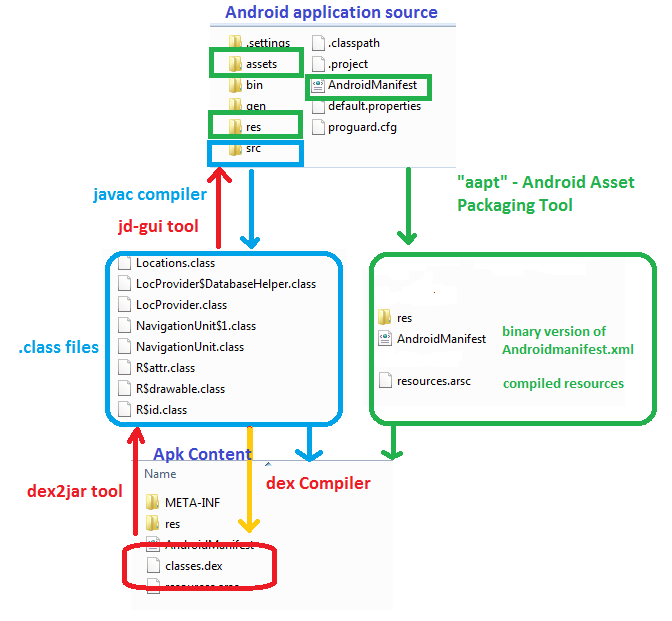
There are a selection of the way to do that, however I favor to make use of the adb command (Android debug bridge) device that comes with the Android Developer Package as a part of the Android SDK. The adb command permits you to pull a duplicate of the APK off the phone onto your PC for additional evaluation.
An APK file is nothing, however, a ZIP file and renaming the APK file as a ZIP file will allow you to open it with any ZIP file explorer. These can be found underneath the /data/app directory. You’ll be able to pull it onto your machine utilizing the adb pull command. In there, you can see the manifest file, resources, assets, and others.
Next, using the dexdump utility provided in Android, the classes under the /data/dalvik-cache directory can be dumped.
For example, to dump data@[email protected]@classes.dex into a file called dump, the command to be used is:
dexdump –d –f –h data@[email protected]@classes .dex > dump
This dump will be in the form of the jump statements and is hard to read. A DEX de-compiler such as baksmali or dedexer can be used to make these files much more readable.


